The answer comes from community safety purposes that carry out lively port scanning and banner grabbing a good way to find out open ports, and the purposes / companies behind them. Such options give prompt visibility into the safety of your server from the outsider's perspective, by mimicking attacker's behavior. Some options collect prolonged details concerning the purposes and companies behind open ports, and in addition indicate potential vulnerabilities which can be exploited. Some companies or purposes operating on open ports could have poorly configured default settings or poorly configured operating policies. Such purposes stands out as the goal of dictionary attacks, and, with poorly configured password policies, for example, attackers can determine credentials utilized by reliable users. Furthermore, attackers can use the credentials to log into such applications, steal data, entry the system, trigger downtime or take management of the computer.
Open ports are utilized by purposes and companies and, as any piece of code, they could have vulnerabilities or bugs. The extra purposes and companies run applying open ports for Internet communication, the upper the danger of 1 of them having a vulnerability that could be exploited. A bug in a single service reachable from the surface could trigger it to crash.
Such a crash might result in execution of arbitrary code on the affected machine, precisely what the attacker wants so we can be successful. These cybercriminals typically use port scanning as a preliminary step when concentrating on networks. They use the port scan to scope out the safety stages of varied organizations and decide who has a robust firewall and who could have a weak server or network. A variety of TCP protocol strategies in reality make it achievable for attackers to hide their community location and use "decoy traffic" to carry out port scans with no revealing any community handle to the target.
Behind open ports, there are purposes and prone listening for inbound packets, anticipating connections from the outside, that allows you to carry out their jobs. Security ultimate practices suggest using a firewall system that controls which ports are opened or closed on Internet-facing servers. Additionally, safety ultimate practices advise that ports must be open solely on a "need-to-be" basis, dictated by the Internet communication wants of purposes and prone that run on the servers. Take a CVE revealed in 2001 that exploited port 3389 over Remote Data Protocol .
Therefore, it really is important for enterprises that don't use RDP over port 3389, be certain this port is closed to scale back the assault floor ultimately. To be clear, all ports and their respective service have some probability of attack. On high of preliminary access, menace actors can leverage open ports to pay attention in, seek for credentials, carry out man-in-the-middle attacks, carry out distant code execution , and exfiltrate statistics in plain sight.
For instance, menace actors could typically use TCP/UDP port 53, utilized by Domain Name System , to exfiltrate files collected contained within the community since DNS visitors is not really commonly tracked. Therefore, an open port fifty three serves as a quiet exit route for adversaries. Scanning instruments utilized by equally attackers and safety professionals enable an automatic detection of open ports. Many network-based IDS/IPS solutions, and even workstation-based endpoint safety options can detect port scanning. It is worthy it to analyze port scanning originating from contained within the nearby network, because it typically means a compromised device. However, desktops operating some safety options can generate false positives.
This is beacause distributors of safety options function a port scanner to detect weak gadgets inside a house network. Security throughout all community ports ought to embrace defense-in-depth. Close any ports you don't use, use host-based firewalls on each host, run a network-based next-generation firewall, and monitor and filter port traffic, says Norby. Do common port scans as a half of pen exams to make definite there are not any unchecked vulnerabilities on any port. Pay explicit consideration to SOCKS proxies or some different service you probably didn't set up.
Patch and harden any device, software, or service related to the port till there are not any dents in your networked assets' armor. Be proactive as new vulnerabilities seem in previous and new program that attackers can attain by way of community ports. As port scanning is an older technique, it requires safety modifications and up-to-date menace intelligence when you consider that protocols and safety resources are evolving daily. As a most advantageous follow approach, port scan alerts and firewalls ought to be used to watch visitors to your ports and be positive malicious attackers don't detect potential chances for unauthorized entry into your network. Each open port will be the goal of denial of service attacks. The crash of the unused NTP service causes system instability and ought to deliver down a whole server.
Thus, an attacker can carry out victorious denial of service assaults on an internet server, with no even concentrating on port 80. SMB is used as a community file sharing protocol, from a pc or server to switch info to different systems. An exploit referred to as EternalBlue in 2017 focused a vulnerability in SMB v1.0 that permits attackers to remotely execute arbitrary code and attain entry into the community as a result of specifically crafted packets. Well-known malware that utilized EternalBlue was WannaCry and Emotet .
This challenge uncovered the highest 10 most uncovered IoT ports, recognized Mirai because the best malware menace to IoT devices, and Gandcrab because the best ransomware threat. The IoT units which might be presumably to be attacked incorporate surveillance systems, IP cameras, webcams, and so on. The IoT structures most susceptible to assault are ICSs, SCADA structures and industrial automation technologies.
The companies which might be most prone to being attacked are FRITZ! Box http config listening on port 443 SSL/HTTPS and OpenSSH listening on a number of ports. The working system that's most prone to being attacked is both Actiontec embedded, Linux 2.4.X or Linux 3.x. This challenge additionally recognized encrypted internet traffic's prevalence over plain textual content traffic. The objective behind port and community scanning is to determine the group of IP addresses, hosts, and ports to accurately decide open or weak server places and diagnose safety levels. Both community and port scanning can reveal the presence of safety measures in place resembling a firewall between the server and the user's device.
All networks are secured by one firewall on the perimeter of the network, and this firewall is configured to allow HTTP and SMTP visitors to cross through. Other software visitors is pressured to make use of a secured tunnel to go by means of the network. Of course, the perimeter firewall is configured to watch the traffic, and a log is stored for analysis. Internal community is constructed utilizing Ethernet segments to mirror the infrastructure of the organization. IP community segments are then superimposed on the Ethernet segments. Each IP community phase is secured from one another by a firewall.
Each of the IP segments is related to the layer-3 switch, thus additional defending every IP phase from an exterior attack. The IP traffics from the layer-3 change are directed to go by means of a Demilitarized ZONE earlier than it enters the perimeter router. The nodes within the DMZ are DNS, SMTP, and HTTP servers, that are permitted for each inbound and outbound traffic. The attacker would scan the ports on the perimeter firewall and search for open ports on the firewall. The firewall would have the ports similar to eighty and 25 (well-known) open for Web and e mail services.
The aim of the attacker is to seek out which ports in "listen," "wait," or "closed" state. Thus, we will be taught addresses for the aim networks' DNS servers, Web servers, and e mail servers. The GFI Languard NSS software program has a utility "whois" that quite simply permits discovering all of the knowledge relating to a website identify registered to a company network. DNS Zone transfers seek advice from researching concerning the servers and their IP addresses from zone files. One of the explanations enterprise leaders wrestle to know cybersecurity threat is that the technical terminology typically feels exterior their wheelhouse. Organizational leaders know the affect of knowledge breaches however examining about how cybercriminals infiltrate networks can really sense like listening to a special language.
For example, a Distributed Denial of Service assault is when cybercriminals use botnets to ship most details to a community that it crashes, resulting in downtime in addition to potential infiltration. However, to mitigate the danger of those attacks, it's essential know what ports are, why cybercriminals use them, and the way to safe dangerous open ports. In fact, the host discovery aspect in community scanning is usually step one utilized by attackers earlier than they execute an attack. Businesses can even use the port scanning procedure to ship packets to targeted ports and analyze responses for any potential vulnerability. They can then use instruments like IP scanning, community mapper , and Netcat to make certain their community and structures are secure. Malicious ("black hat") hackers frequently use port scanning software program to seek out which ports are "open" in a given computer, and even if or not an real service is listening on that port.
They can then try and exploit potential vulnerabilities in any providers they find. Malicious ("black hat") hackers often use port scanning software program to seek out which ports are "open" in a given computer, and regardless of whether or not an precise service is listening on that port. That is true, however there's additionally a cause attackers are likely to focus on the three ports they do. Most of the ports are unassigned and obtainable for purposes and providers to make use of to speak throughout the network, however a few ports are reserved and designated for certain protocols or services. For example, FTP makes use of ports 20 and 21, and SMTP makes use of port 25 by default.
Sometimes when an attacker is testing out software program for command execution, or distant file examine skills they are going to insert characters to assist obtain this goal. Sometimes scripts can not deal with this extra information insertion nicely and as an alternative terminate abnormally. Often occasions customers who addContent scripts, which aren't configured accurately for this unique system , may give this error. An attacker with community entry to the online server on port 80/TCP or 443/TCP might execute system instructions with administrative privileges.
The safety vulnerability might be exploited by an unauthenticated attacker with community entry to the affected service. No consumer interplay is required to take advantage of this safety vulnerability. Successful exploitation of the safety vulnerability compromises confidentiality, integrity or availability of the focused system.
At the time of advisory publication no public exploitation of this safety vulnerability was known. Other non-HTTPS and non-HTTP ports within the highest 10 are ports 21 and 25. There are 30,059 hosts with port TCP 21 FTP exposed, a plain-text protocol used for transferring information throughout the Internet. FTP should be utilized by IoT gadgets to switch files to an software server or gateway. The distinction is that as opposed to scanning one system on a number of ports, with portsweeping, a number of programs are scanned on the identical port. For example, in the event you wish to take advantage of a specific SQL vulnerability, it's essential discover which programs are operating SQL Server.
You can use portsweeping to scan a community for techniques which could doubtlessly be exploited. Is used to find out what ports a system can be listening on. This will assist an attacker to find out what companies can be operating on the system. Some port scanners scan by ports in numeric order; some use a random order.
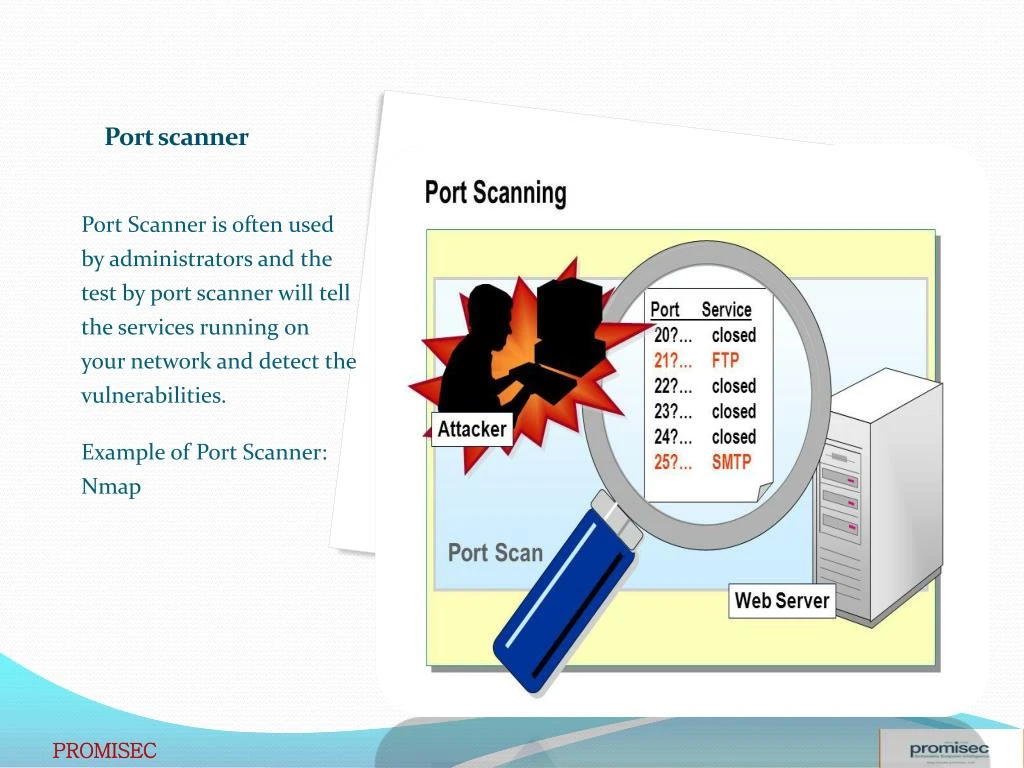
There are many various techniques used for port scanning, which includes SYN scanning, ACK scanning, and FIN scanning. A port scan is a standard methodology hackers use to discover open doorways or weak factors in a network. A port scan assault helps cyber criminals discover open ports and work out even if or not they're receiving or sending data. It may additionally reveal even if lively safety instruments like firewalls are getting utilized by an organization. This emphasizes the significance and safety advantages of limiting the allowed outgoing communication from the several servers and processes in your statistics center. Namely, figuring out communication to a vacation spot port for the primary time, from a course of that up to now has communicated over a selected set of ports, can be valuable to establish assault attempts.
We proceed this line of exploration on a extra granular foundation for a number of regularly occurring Java applications. HTTP and HTTPS are application-layer protocols used for communication between net browsers and net servers. HTTP permits attackers to listen in on usernames and passwords in cleartext.
On the opposite hand, HTTPS includes encryption that creates an encrypted tunnel each time knowledge packets are communicated over the community so adversaries are unable to eavesdrop or intercept knowledge communication. This port will mainly be open solely when an internet server of some type is operating on the machine. However, as one can see from the huge listing of Trojan sightings below, there isn't a scarcity of malicious program attempting to inhabit this port. The widespread Code Red and Nimda worms are nonetheless alive, and are extra most likely to outlive out on the Internet for a lot of extra years. They proceed attempting to find weak methods into which they could reproduce wherever and at any time when possible. And then, any publicly accessible internet servers have to be proactively maintained and stored existing with the newest safety patches to maintain them safe.
Many assaults are low and slow, creating command and management channels that permit them to exfiltrate extra files and stay undetected for longer durations of time. The complexity of networks, and the multitude of open ports throughout a corporation make figuring out threats extra and extra difficult. The simplest, most straightforward, and costliest strategy is a reactive stance the place you look ahead to some factor to ensue and repair it. The most efficient answer is to proactively scan and analyze the community infrastructure.
Tenable.io permits analysts to match identified open ports between scans. New lively ports and vulnerabilities should be detected, avoiding potential blind spots the place new prone are put in or enabled. Due to such a lot of vulnerabilities within the sooner variants of the SMB protocol, it was exploited by menace actors within the exceptionally publicized WannaCry ransomware attack. Computers contaminated with WannaCry scanned its community for instruments accepting visitors on SMB ports to hook up with them and unfold the malware. Internet-facing prone and purposes primarily pay attention on ports for a connection from the surface to do their jobs.
Without ports, communication between hosts over the web isn't possible. EternalBlue has been used equally because the preliminary vector of assault and as a option to carry out lateral motion after a community has been infiltrated. The exploit works when attackers ship crafted packets to a system operating SMBv1. In the case of WannaCry, attackers exploited the vulnerability by loading malware on the weak goal system after which spreading that malware by way of the identical vulnerability to different methods on the network.
EternalBlue was additionally utilized within the NotPetya assaults and as component of the TrickBot malware Trojan. Insecure ports imply pointless companies are listening on the community that both use insecure protocols or permit exploitation by default, or by being misconfigured. Even safe open ports can doubtlessly be abused or grant details concerning the system to attackers. Any internet-connected service requires targeted ports to be open with a view to function. If Nmap receives an ICMP unreachable error it'll report the port as filtered.
Is Port 80 Insecure These superior port scanning possibilities are stealthy and should bypass firewalls and different safety controls. However, most host- and network-based intrusion detection structures will detect such a scan activity. Keep in thoughts that OSes that don't comply with the TCP RFC might ship deceptive responses. We have already mentioned the importance of TCP and UDP port numbers, and the well-known and never so well-known prone that run at these ports. Each of those ports is a possible entryway or "hole" into the network. If a port is open, there's a service listening on it; well-known prone have assigned port numbers, corresponding to http on TCP port eighty or telnet on TCP port 23.
Port scanning is the method of sending packets to every port on a system to discover which of them are open. You'll mostly detect scans and sweeps from Script Kiddies or different automated, semi-intelligent attacks. More skilled Black Hats will scan extra slowly, normally sluggish sufficient to avert being detected by a firewall. This strategy of sending port scanning packets occasionally over an extended time interval is called a sluggish scan. Preventing a port scan assault is reliant on having effective, up to date menace intelligence that's according to the evolving menace landscape. Businesses additionally require sturdy safety software, port scanning tools, and safety alerts that monitor ports and stop malicious actors from reaching their network.
Port scanning is a well-liked technique cyber criminals use to seek for weak servers. They normally use it to find organizations' safety levels, decide regardless of whether companies have valuable firewalls, and detect weak networks or servers. Some TCP techniques additionally allow attackers to cowl their location. It is very primary to comprehend the negative aspects of operating a community application.

















No comments:
Post a Comment
Note: Only a member of this blog may post a comment.